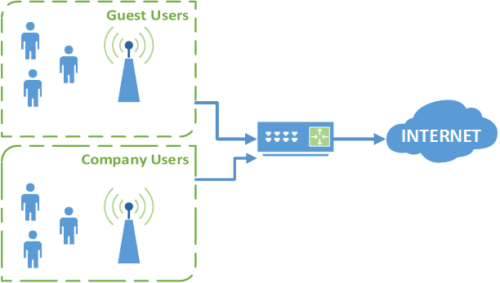
Many businesses make a common mistake of not using a guest network to secure their WIFI. Many say no one will look close enough to find a way in. What you need to remember is people are looking, and your WIFI could be accessed from the parking lot. The most basic way to keep your business secure is by turning on a isolated guest WIFI for customers.
Specifically, it gives visitors access to your Internet connection and nothing else. They can’t see any of your devices on the network and they don’t have the ability to access them. Most importantly, they can’t accidentally introduce malware or compromise your devices or data in any other way.
Why Is Having a Guest Network Important?
You may think it is not a big deal but private networks lack security by default. Most device lower their security and open up services, access and network shares on traffic in a private network. Basically your workstation by default will trust devices on your wifi… Even customers or the hacker in the parking lot.
Securing these devices may make some functions you need much more complicated to use. Especially file sharing. That is why a isolated guest network in so convenient as to allow your workstations to remain secure and your employees personal phones and customers to access the guest network.
Hackers want your data. They want to control your devices, force you to pay for release, sniff around for interesting data, steal your identity, that kind of thing.
Setting up a guest network on supported routers is simple. Enabling the feature improves security, keeping your activity private and secure. It helps to prevent unauthorized access and intrusion on your network, protecting the data you send and receive.
Is A Guest Network Just For The Public?
No! Only company owned devices should be on the private network. Employees should not know the password, and should not connect their phones or personal devices. This is because one infected device can spread to other networked devices. It also means that once terminated an employee may be able to access your network to cause trouble.